Overview of VMware NSX Architecture

VMware NSX Architecture is simply an added product that allows you to install and manage virtual networking and security devices inside your existing VMware cloud. VMware acquired this technology from Nicira in 2012. This acquisition launched VMware into the software-defined networking (SDN) business and cemented their position as the number 1 cloud hypervisor today.
The VMware NSX architecture can create distributed virtual switches, distributed logical routers, logical switches (VXLANs), load balancers, firewalls, and VPNs. This simply replaces the traditional hardware ones used in today’s environments.
Having NSX as your software defined network means you can automate and containerize your deployments much easier and faster. This enhancement will revolutionize the VMware cloud as we know it and move them forward in many ways. This includes scaling production environments on demand and increasing security by leaps and bounds
The security benefits cannot be understated. NSX deploys micro-segmentation that allows the security team to easily apply custom security rules for each virtual device and managed them centrally. These firewalls, switches, and routers are controlled at the hypervisor level. This design provides better protection to the virtual device and the rest of your environment from threats inside and outside your network.
So why isn’t everyone deploying NSX? Simple. It is very complicated. I will be writing several articles over the next few weeks and months and cover NSX in extreme detail and provide you with all the information you need to deploy it and manage it in your environment.
Benefits of NSX include the following features:
- DataCenter automation
- Self-service networking services
- Rapid application deployment with automated network and service provisioning
- Isolation of development, test, and production environments on the same bare metal infrastructure
- Single Account multi-tenant clouds
NSX can be configured and managed through the vSphere Web Client, a command line interface (CLI), MS PowerShell (PowerCLI), and REST API. The core network services offered by NSX are listed below.
Core NSX Services
Logical Switches
A cloud deployment might have a variety of applications across multiple tenants. These applications and tenants require isolation from each other for security, fault isolation, and avoiding overlapping IP addressing issues. The NSX logical switch creates segments (VXLAN / vWires) to which an application or virtual machine can be logically connected. It communicates to each host using vTEP ports on each host which intercept layer 2 communications on the logical switch, encapsulated them, and then routes them to each host. The receiving host decapsulates the packet and treats the data as a standard layer 2 packet.
This allows for flexibility and speed of deployment while still providing the characteristics of a physical network’s broadcast domains (VLANs). Logical switches allow for thousands of tenant networks to be provisioned onto a single Private Network (VLAN). A logical switch is distributed and can span large compute clusters, even across different physical networks. This allows for virtual machine mobility within the data center and beyond) without limitations of physical Layer 2 boundaries.
Distributed Logical Routers
Dynamic routing provides the necessary forwarding information between layer 2 broadcast domains (VXLAN / vWires / Logical Switches), allowing you to decrease layer 2 broadcast domains and improve network efficiency and scale. NSX extends this intelligence to where the workloads reside for providing East-West routing functions. This allows more direct virtual machine to virtual machine communication without the costly or timely need to extend hops. At the same time, NSX also provides North-South connectivity inbound/outbound of data centers, thereby enabling tenants to access public networks securely and efficiently.
Logical Firewall
Logical Firewall provides security mechanisms for dynamic virtual data centers. The Distributed Firewall component of a NSX Logical Firewall allows you to segment virtual datacenter entities, like virtual machines, based on VM names and attributes, user identity, vCenter objects like DataCenters and hosts, as well as traditional networking attributes like IP addresses, VLANs, etc. The Edge Firewall component helps you achieve key perimeter security needs such as building DMZs based on IP/VLAN constructs, tenant to tenant isolation in multi-tenant virtual data centers, Network Address Translation (NAT), VPNs, and User based SSL VPNs. Edge Firewalls can be leveraged in combination with physical firewalls for perimeter protection. The Firewall Flow Monitoring feature displays network activity between virtual machines at the application protocol level. You can use this information to audit network traffic, define and refine firewall policies, and identify threats to your network.
Logical Virtual Private Networks (VPNs)
SSL VPN-Plus allows remote users to access private corporate applications. IPSec VPN offers site-to-site connectivity between an NSX Edge instance and remote sites. L2 VPNs allow you to extend your datacenter by allowing virtual machines to retain network connectivity across geographical boundaries.
Logical Load Balancer
The NSX Edge load balancer enables network traffic to follow multiple paths to a specific destination. It distributes incoming service requests evenly among multiple servers in such a way that the load distribution is transparent to users. Load balancing thus helps in achieving optimal resource utilization, maximizing throughput, minimizing response time, and avoiding overload. NSX Edge provides load balancing up to Layer 7.
NSX Edge Gateway
The NSX Edge provides network edge security and gateway services to isolate a virtualized networks. You can install an NSX Edge either as a logical (distributed) router or as a services gateway. The NSX Edge logical (distributed) router provides East-West routing with tenant IP address space and data path isolation. Virtual machines or workloads that reside on the same host on different subnets can communicate with one another without having to traverse a traditional routing interface. The NSX Edge Gateway connects isolated stub networks to shared (uplink) networks. It can also provide common gateway services such as DHCP, VPN, NAT, dynamic routing, and Load Balancing. Common deployments of NSX Edge include in the DMZ, VPN Extranets, and multi-tenant cloud environments where the NSX Edge creates virtual boundaries for each tenant.
NSX vSwitch
NSX vSwitch is the software that operates on ESXi hosts to form a software abstraction layer between servers and the physical network. As the demands on data centers continue to grow, requirements related to speed and access to the data itself continue to grow as well. In most infrastructures, virtual machine access and mobility usually depend on physical networking infrastructure and the physical networking environments they reside in. NSX vSwitch allows you to place these virtual workloads on any available infrastructure in the data center, regardless of the underlying physical network infrastructure. This not only allows increased flexibility and mobility, but increased availability and resilience.
Service Composer
Service Composer helps you provision and assign network and security services to applications in a virtual infrastructure. These services can be mapped and applied to virtual machines in the security groups. Data Security provides visibility into sensitive data stored within your organization’s virtualized and cloud environments. Based on the violations reported by NSX Data Security, you can ensure that sensitive data is adequately protected and assess compliance with regulations around the world.
NSX Extensibility
VMware partners can integrate their network service solutions with the NSX platform. This enables customers to have an integrated experience across VMware products and partner solutions. Data center operators can provision complex, multi-tier virtual networks in seconds, independent of the underlying network topology. Cisco, F5, and several virtual FW solutions are examples of how NSX can support other services. Non-networking solutions include antivirus and VM level backup solutions which are very common today.
NSX Core Components
This section describes the core NSX components that would be installed in a typical NSX deployment. VMware NSX recommends a dedicated management cloud environment with at least vCenter & ESXi deployed on vSphere 6.x.
NSX Manager
The NSX Manager is the centralized network management component of NSX. It is installed as a virtual appliance on an ESX host in your vCenter Server management cluster. One NSX Manager maps to a single vCenter Server environment. This is the key component and should have regular backups.
NSX Controller
NSX controller is an advanced distributed state management system that controls virtual networks and VXLAN overlay transport tunnels. The controller is the central control point for all logical switches within a network. It maintains information of all virtual machines, hosts, logical switches, and VXLANs. The controller supports three logical switch control plane modes, Multicast, Unicast, and Hybrid. These modes decouple NSX from the physical network.
The NSX Controller(s) will utilize Unicast mode with virtual tunnel endpoints (VTEPS) to provide mac learning and other functions. This allows VXLAN Broadcast, Unknown unicast, and Multicast (BUM) traffic within a logical switch. The unicast mode replicates all the BUM traffic locally on the host and requires no physical network configuration outside of Layer 3 connectivity between VTEPS. The NSX manager deploys at least 3 controllers to manage the environment. All of the nodes are deployed as virtual machines and are managed by the NSX Manager on an ESX Management Cluster.
NSX Edge
NSX Edge provides network edge security and gateway services to isolate a virtualized networks. You can install an NSX Edge either as a logical (distributed) router or as a services gateway. The NSX Edge logical (distributed) router provides East-West distributed routing with tenant IP address space and data path isolation. Virtual machines or workloads that reside on the same host on different subnets can communicate with one another without having to traverse a traditional routing interface. The NSX Edge Gateway connects isolated stub networks to shared (uplink) networks by providing common gateway services such as DHCP, VPN, NAT, dynamic routing, and Load Balancing. Common deployments of NSX Edge include in the DMZ, VPN Extranets, and multi-tenant cloud environments. This is where the NSX Edge creates virtual boundaries for each tenant.
VMware NSX Architecture
The design is rather simple to understand but very complicate to manage and troubleshoot. VMware NSX is a very powerful platform and requires a dedicated cluster or farm. The NSX manager is the heart of NSX and will be available similar to a normal plugin on the vCenter server. One limitation is NSX will only communicate with just a single vCenter server. If you are deploying the NSX-T version, then it will run as a standalone server.
NSX will deploy controllers to manage the switches and will deploy special kernel level software on each host. This allows for the networking devices to run on each ESXi host. Once the product is configured and running, management will be divided between the NSX manager and the routers and switches that were deployed (like in a regular physical network). The main difference is now everything is virtual.
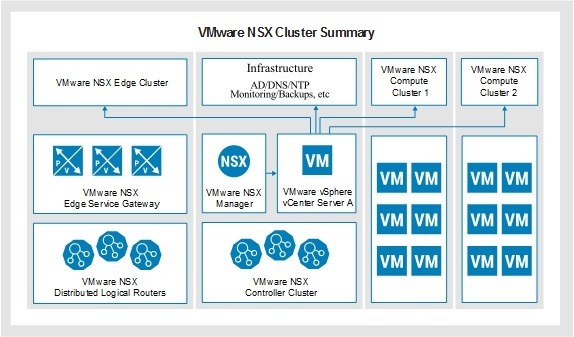
Remember that NSX was created by a 3rd party company and bought by VMware in 2012. NSX is easy to understand how it functions inside the vSphere architecture when you see it as a separate product and not natively apart of vSphere. It is pretty self contained and will issue commands to the VC using standard VC API or communicate to the NSX controllers for other tasks. In affect, it is almost like SRM in how it works from a communication flow perspective.
I will create a separate article about how logical switching and routing works. I will post a link to it here.
Conclusion
Having worked as a network administrator in the past and now as a Cloud NSX administrator, I can say a NSX environment is much more complicated for one simple reason. Instead having fewer but larger switches and routers, we now have lots of logical routers and switches per customer which often adds up to well more then several hundred per data center. The quantity of devices is what’s providing our security micro-segmentation.
This growth in devices multiplies the work and management by an incredible amount but the security and performance also increases dramatically in a SDN environment. We now have the ability to completely isolate not only customers from each other (we always had very strong security between customers), we can now place many security zones inside each customer. In the world we live in today, more security is needed to protect our customers from the ever increasing threats that we face everyday and NSX can do this perfectly.
What is your experience with VMware NSX architecture and have you deployed it in your environment? Do you have any overview related questions I didn’t cover in the article? If you do, please feel free to place the question in the comment section below and I will be happy to answer it. Please sign up to my email list to know when future articles are released.

I like the valuable info you provide in your articles.
I will bookmark your weblog and check again here regularly.
I’m quite certain I will learn many new stuff right here!
-Annis